Payez et Encaissez vos factures en 1 clic
La solution pour centraliser, valider, payer ou vous faire payer, et piloter votre trésorerie efficacement.
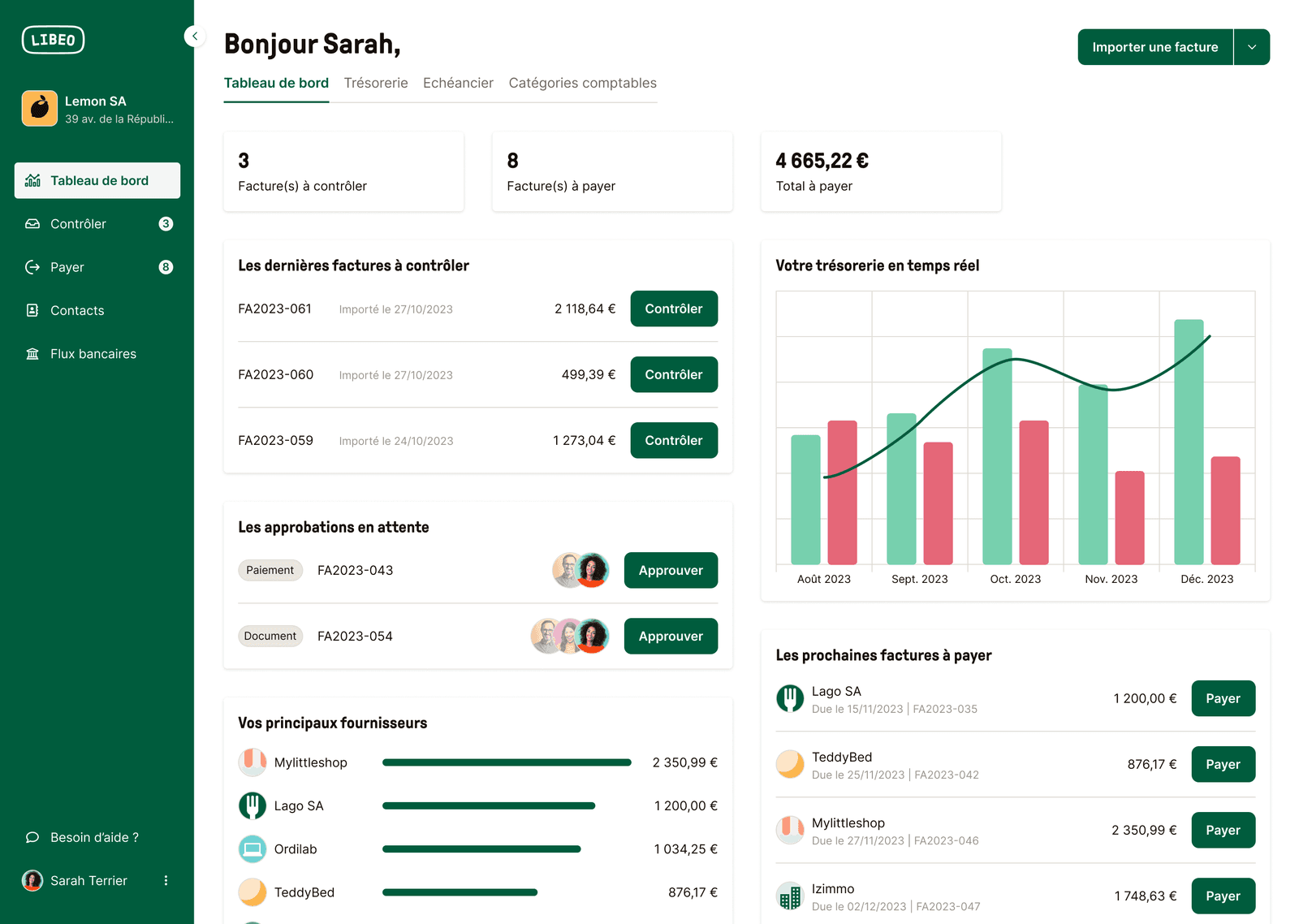


Gagnez 5h par semaine dans votre gestion
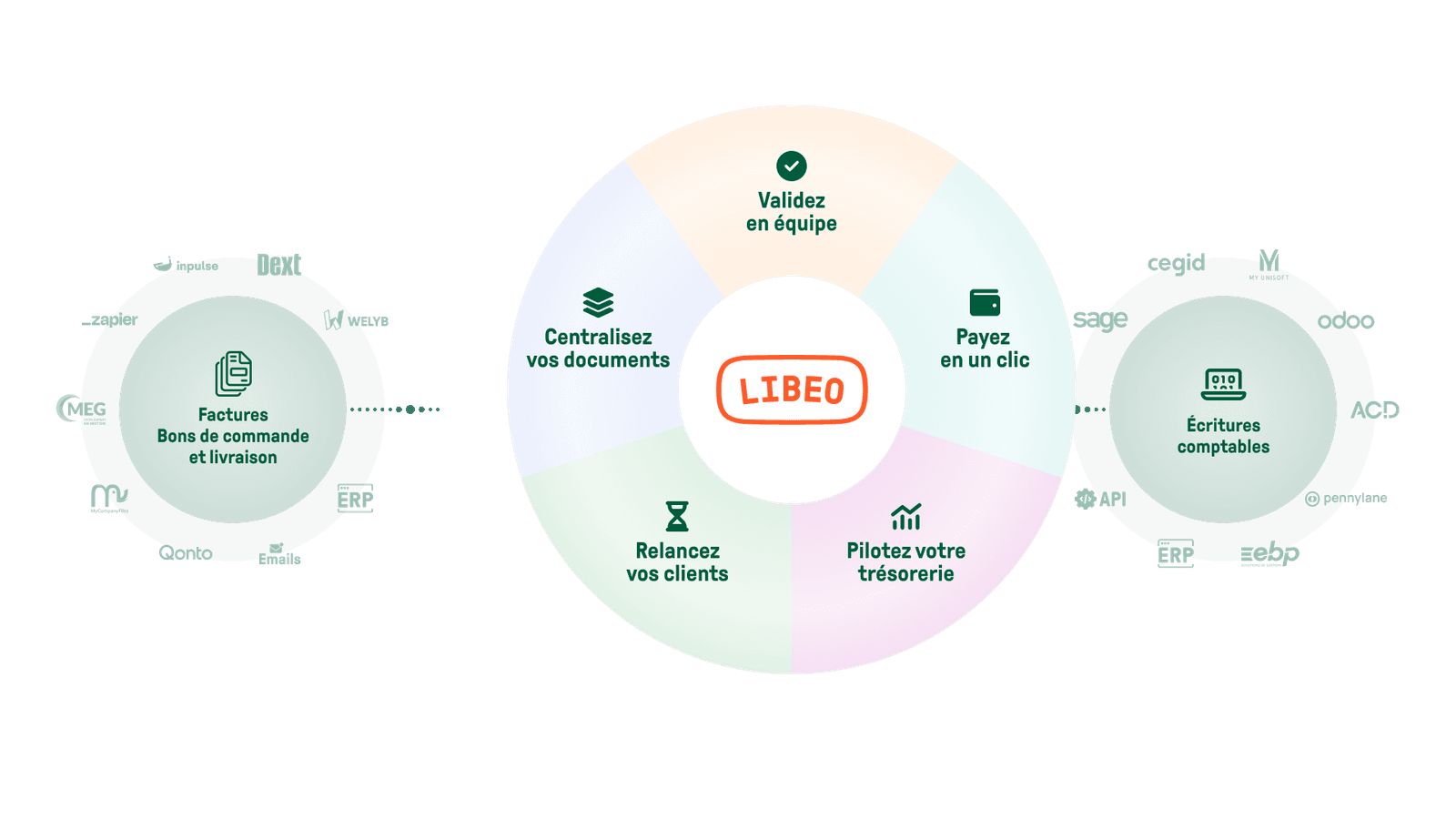
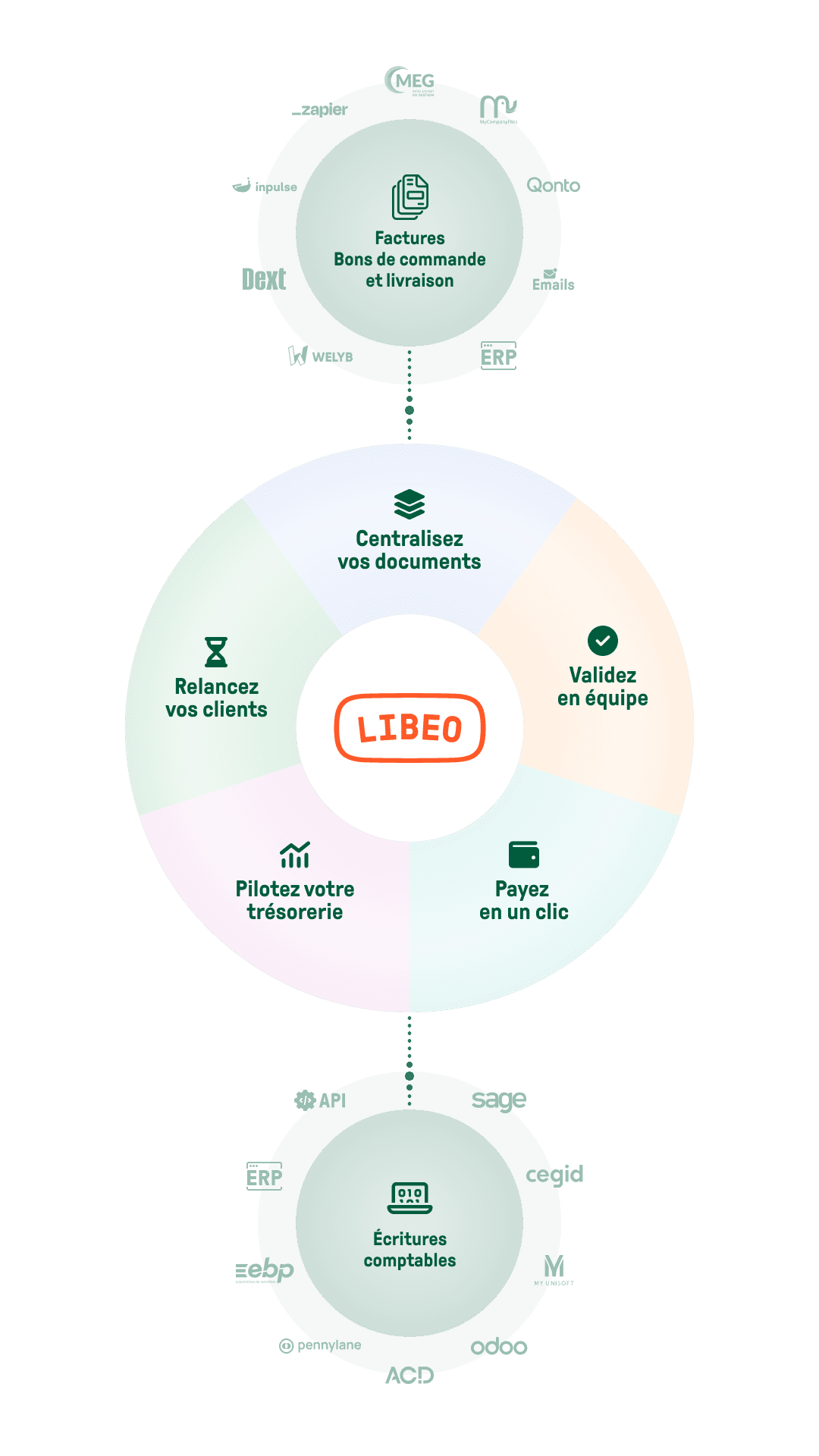
Dites adieu à la saisie manuelle et aux Excel !
Centralisation
Gagnez du temps sur la collecte de documents
Centralisez toutes vos factures et bons de commande au même endroit, et partagez-les en temps réel avec votre expert-comptable.
En savoir plus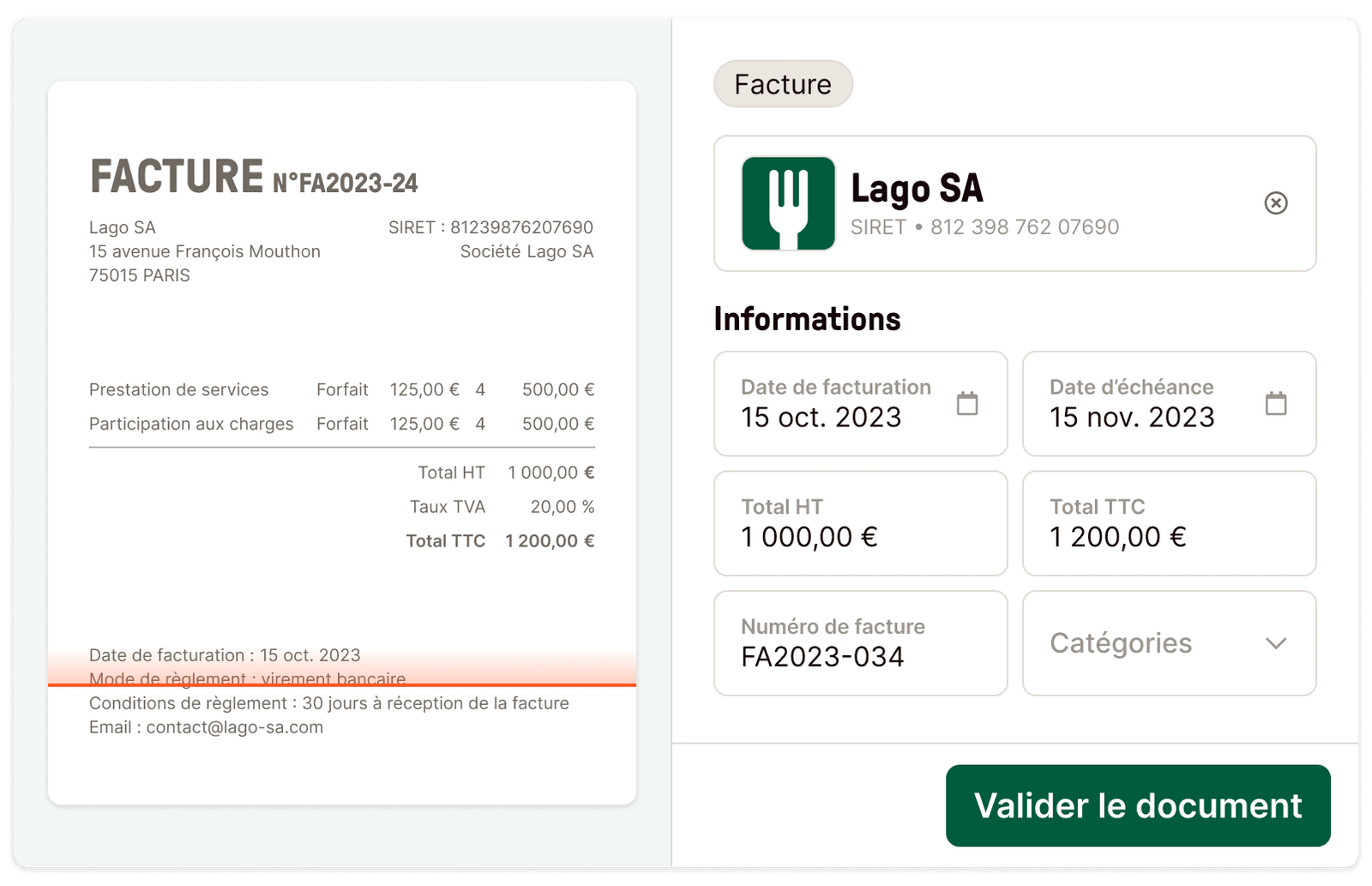
Workflows d'approbation
Contrôlez vos dépenses en équipe
Définissez vos circuits de validation, personnalisez vos règles d’automatisation et maîtrisez enfin toutes vos dépenses.
En savoir plus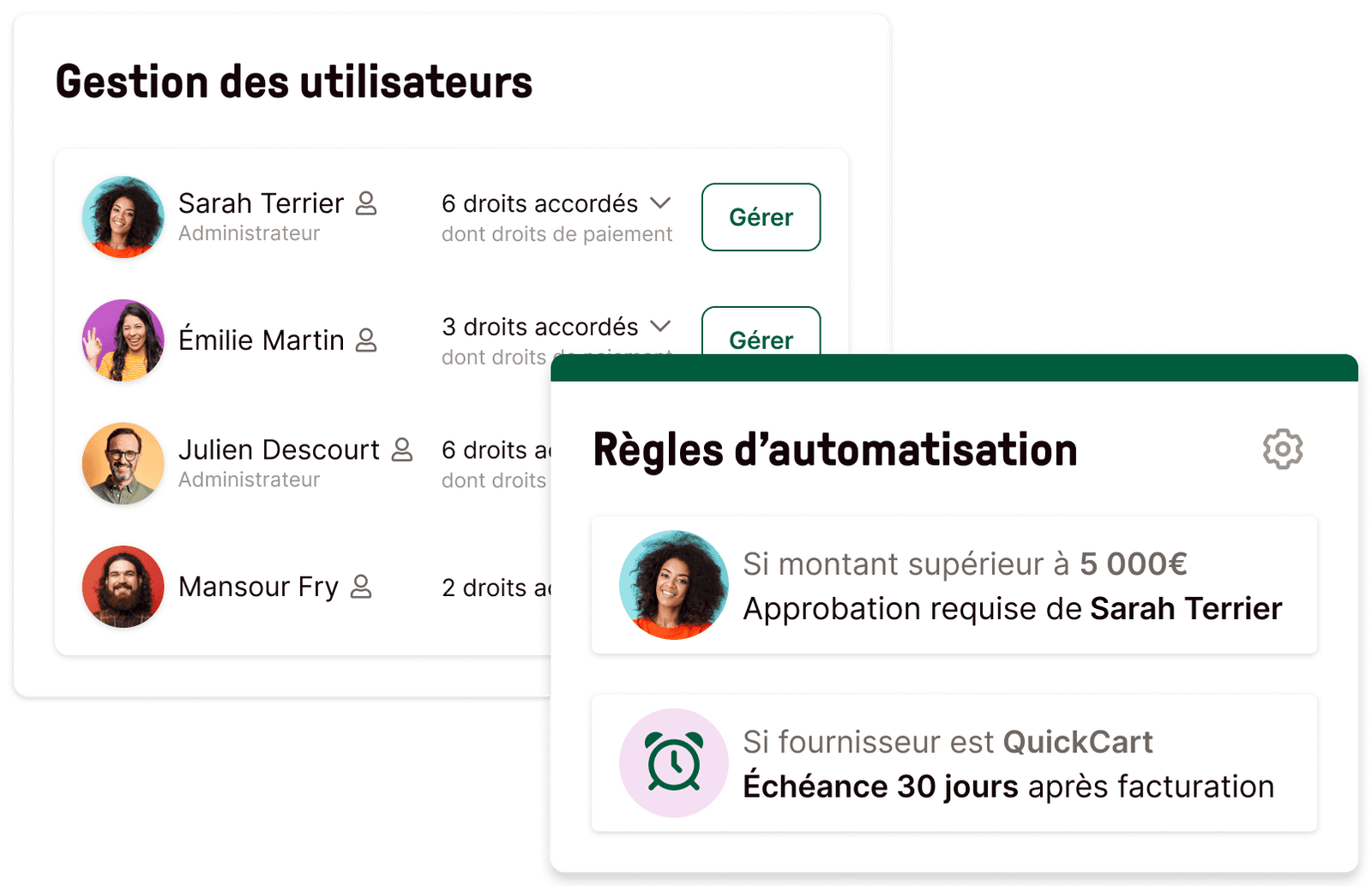
Paiement
Payez en un clic tous vos fournisseurs
Programmez vos paiements à la date de votre choix et exécutez-les depuis votre espace Libeo, sans passer par votre portail bancaire.
En savoir plus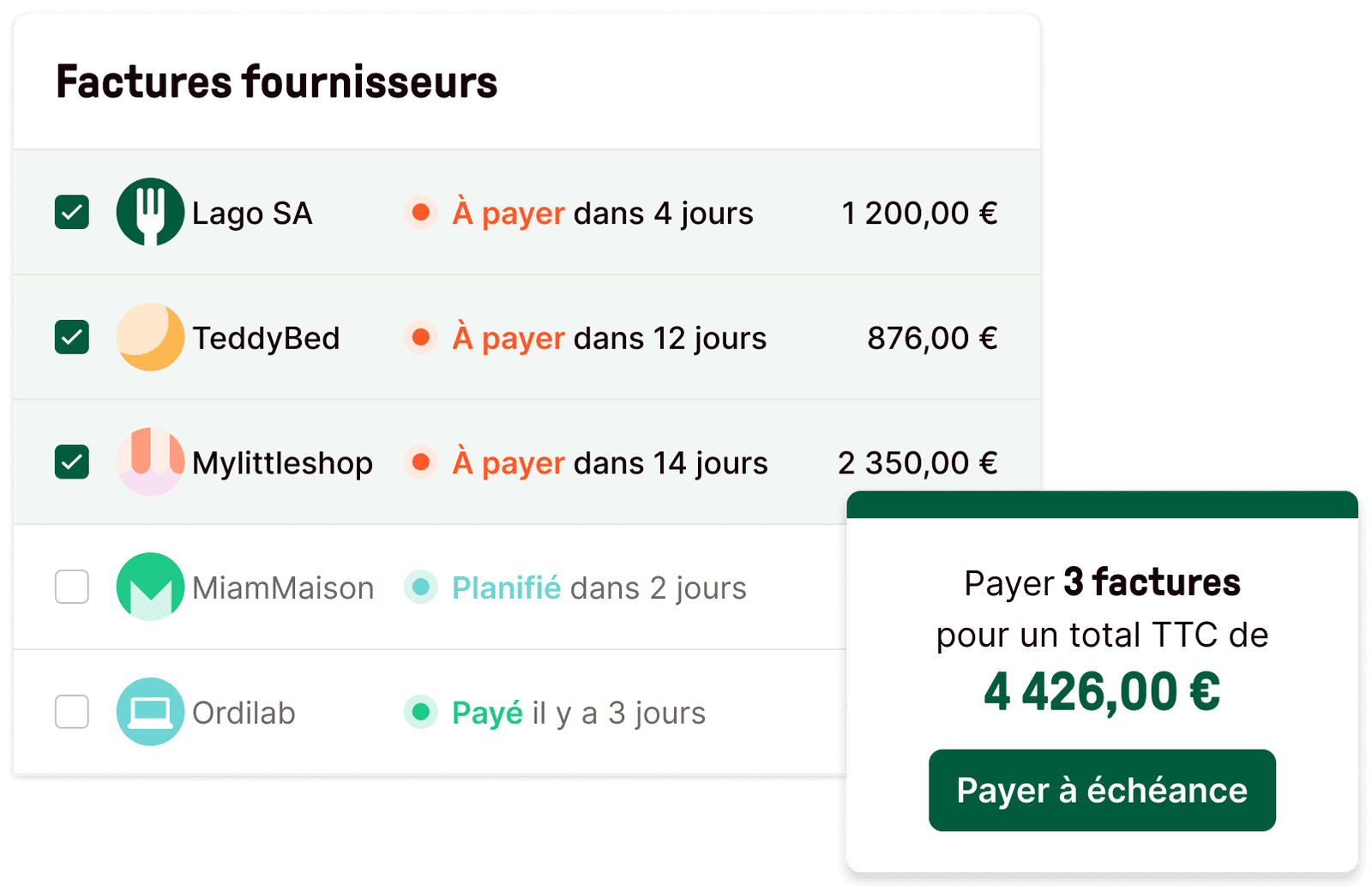
Intégrations
Récupérez et envoyez vos documents, automatiquement
Récupérez vos documents depuis votre logiciel comptable ou votre outil de gestion des stocks, et envoyez vos données vers l'outil de votre expert-comptable, sans qu'il ait besoin de vous solliciter.
En savoir plus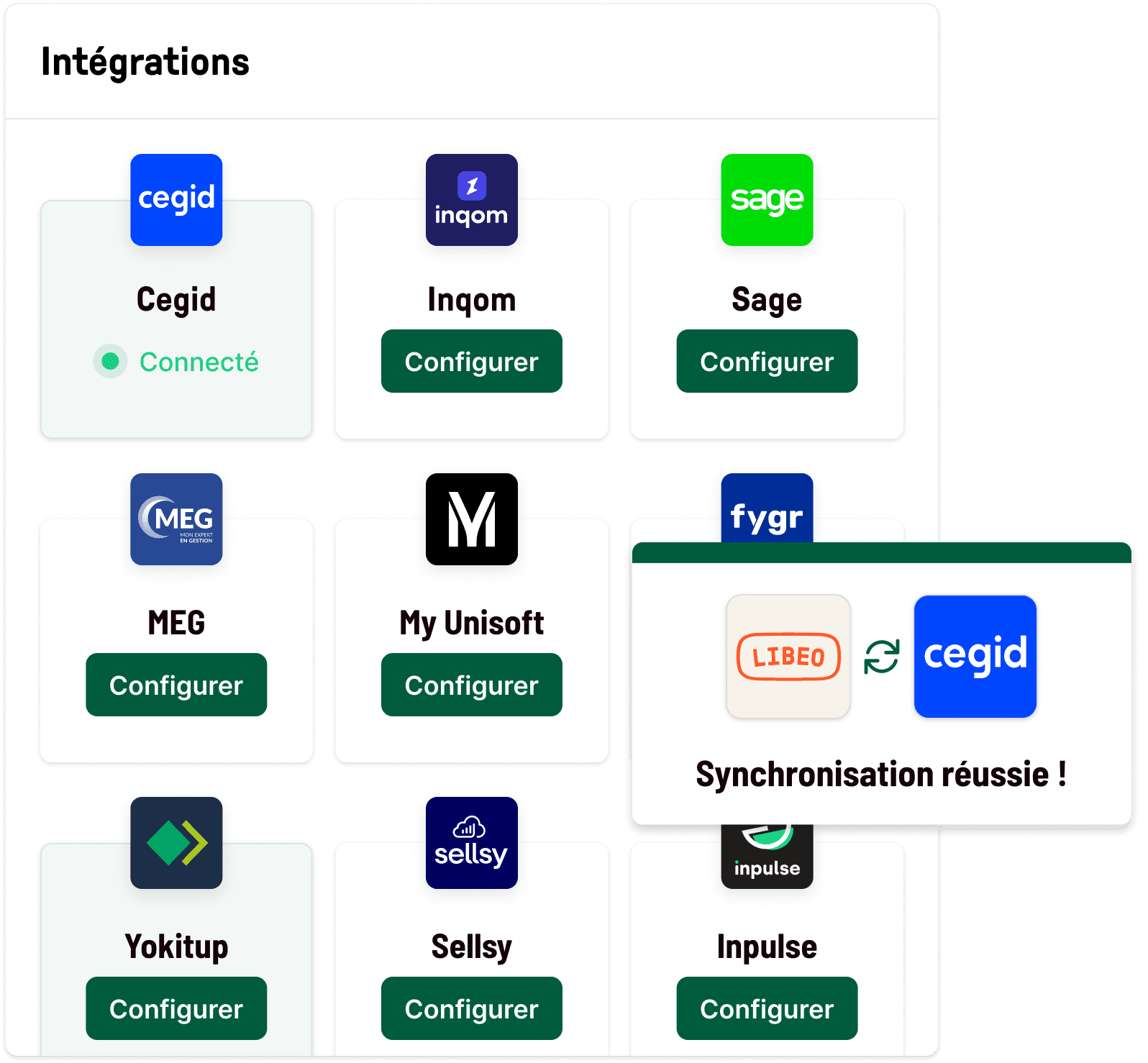
Finie la course aux encaissements
NouveauFAITES-VOUS ENFIN PAYER RAPIDEMENT
Personnalisez vos relances clients automatiques, faites-vous payer et recouvrez si besoin !
Essayer gratuitementRejoignez Libeo et ses 400 000 entreprises
Des entreprises de toute taille utilisent chaque jour Libeo

TPE & PME
Optez pour l'efficacité d'un seul outil pour la gestion des achats et de leur pré-comptabilité.

Groupes & franchises
Facilitez la gestion de toutes vos entités grâce à des vues consolidées sur leurs flux financiers.

Experts-comptables
Connectez Libeo à vos outils de production comptable et offrez à vos clients la meilleure solution pour gérer leur poste fournisseurs.
Sans Libeo, Côté Sushi n'aurait pas été en mesure d'assumer le développement qu’il a connu ces dernières années. Aujourd'hui, ce sont plus de 20 millions d'euros qui transitent par Libeo chaque année.

Emmanuel Taïb
CEO
Il me suffit d'appuyer sur un bouton pour tout valider : l'ensemble de mes factures sont réglées en un clic.

Marcel Nakam
Directeur Général
J’ai vu un changement d’organisation drastique : mon propre reporting sort plus vite et de meilleure qualité. Au moins c’était clair : on va aider les gens à mieux payer.

Caroline Soubils
Experte-comptable

Libeo nous permet de centraliser et contrôler facilement nos factures. Nos circuits de validation sont automatisés et sécurisés.

Elise Erbs
CFO
On avait du mal à suivre les paiements de nos factures. Il nous arrivait parfois de payer nos fournisseurs en double. Sans Libeo, on aurait jamais mis le doigt dessus.

Benjamin Cohen
Fondateur

Libeo est une solution gagnant-gagnant pour nos clients et pour nous. Elle permet de gagner du temps et mieux suivre nos clients au quotidien.

Rachel Chicheportiche
Collaboratrice comptable

Je ne comprends pas pourquoi tous les hôtels de France n'utilisent pas Libeo. J'en viens maintenant à intégrer tous les fournisseurs, même la quittance de loyer de mon hôtel.

François Dapremont
Propriétaire
Payer mes fournisseurs en 1 clic, ça m’a changé la vie.

Cécile Gracianette
Responsable Audit et Gestion

Aujourd'hui, je paie plus de la moitié de mes fournisseurs avec Libeo. Comme on a beaucoup de petits producteurs qui ne travaillent pas avec ce mécanisme de prélèvement, on les paie avec Libeo et c'est très apprécié.

Jean-Michel Roulet
Gérant

Sans Libeo, Côté Sushi n'aurait pas été en mesure d'assumer le développement qu’il a connu ces dernières années. Aujourd'hui, ce sont plus de 20 millions d'euros qui transitent par Libeo chaque année.

Emmanuel Taïb
CEO
Il me suffit d'appuyer sur un bouton pour tout valider : l'ensemble de mes factures sont réglées en un clic.

Marcel Nakam
Directeur Général
J’ai vu un changement d’organisation drastique : mon propre reporting sort plus vite et de meilleure qualité. Au moins c’était clair : on va aider les gens à mieux payer.

Caroline Soubils
Experte-comptable

Libeo nous permet de centraliser et contrôler facilement nos factures. Nos circuits de validation sont automatisés et sécurisés.

Elise Erbs
CFO
On avait du mal à suivre les paiements de nos factures. Il nous arrivait parfois de payer nos fournisseurs en double. Sans Libeo, on aurait jamais mis le doigt dessus.

Benjamin Cohen
Fondateur

Libeo est une solution gagnant-gagnant pour nos clients et pour nous. Elle permet de gagner du temps et mieux suivre nos clients au quotidien.

Rachel Chicheportiche
Collaboratrice comptable

Je ne comprends pas pourquoi tous les hôtels de France n'utilisent pas Libeo. J'en viens maintenant à intégrer tous les fournisseurs, même la quittance de loyer de mon hôtel.

François Dapremont
Propriétaire
Payer mes fournisseurs en 1 clic, ça m’a changé la vie.

Cécile Gracianette
Responsable Audit et Gestion

Aujourd'hui, je paie plus de la moitié de mes fournisseurs avec Libeo. Comme on a beaucoup de petits producteurs qui ne travaillent pas avec ce mécanisme de prélèvement, on les paie avec Libeo et c'est très apprécié.

Jean-Michel Roulet
Gérant

Les forces de Libeo

Service client personnalisé
Bénéficiez de l’accompagnement d’un chargé de compte dédié pour déployer Libeo.
Expérience de paiement unique
Libeo permet de payer les factures en un clic, à partir d’une simple adresse email, sans saisir d’IBAN ni avoir besoin de se connecter à sa banque.
Prise en main rapide
Libeo est la plus solution ergonomique du marché qui vous permet d’être autonome en moins d’une demi-journée.
Lutte contre la fraude
Réglementée par l’ACPR, Libeo sécurise les transactions et réduit le risque de fraude et d’erreurs humaines.
Technologie robuste et éprouvée
Premier outil européen breveté pour le paiement fournisseurs, Libeo est disponible dans plus de 40 pays.
Aucune commission ni frais cachés
Votre abonnement s'adapte à votre usage, pour vous offrir le meilleur service, au meilleur prix.